Navigating KYB: A Guide to B2B Software Development
Every successful business knows the importance of building and maintaining strong partnerships with other companies. Partnerships can provide companies with access to resources, new markets, and new technology solutions. But let's face it: no one wants to enter a collaboration without knowing their potential partner's background.
That's why it’s essential for business owners and CEOs to practice KYB – Know Your Business. Before entering into any kind of business partnership – whether it’s a new distributor or an investor – companies should do their research. They should trace the financials, customer experience, and reputation of any potential partner. A thorough investigation ensures that both parties are getting into a mutually beneficial relationship with minimal risk.
KYB software streamlines the collection and analysis of data from business accounts. It helps owners to be more informed about their potential partners and allows them to make better business decisions. Plus, KYB software saves time and money by eliminating manual processes associated with customer account management.
At Erbis, we have strong expertise in developing KYB software. In this post, we will share it with those who want to create a similar project.
What do KYB and KYC mean in business?
The KYB process involves verifying multiple facts about the business, such as its locations, industry, customer base, etc. It also involves collecting information relating to financial activities and verifying them to ensure that all transactions are safe and secure. By understanding the structure and operations of the target company, it is easier to identify any associated potential risks. This helps avoid destructive business relationships and protect your own business in the long term.
The importance of KYB goes hand in hand with KYC (Know Your Customer) – they are two complementary processes that help protect organizations and their customers from financial crime.
At its core, KYB is all about understanding other companies' businesses, how they operate, and how they earn money. This includes things like ownership structure, beneficiaries structure, stakeholders hierarchy, revenue models, etc. And if you want to dig deeper for information about a specific person - for example, a founder or co-owner of a company - you can do so with the KYB's help also.
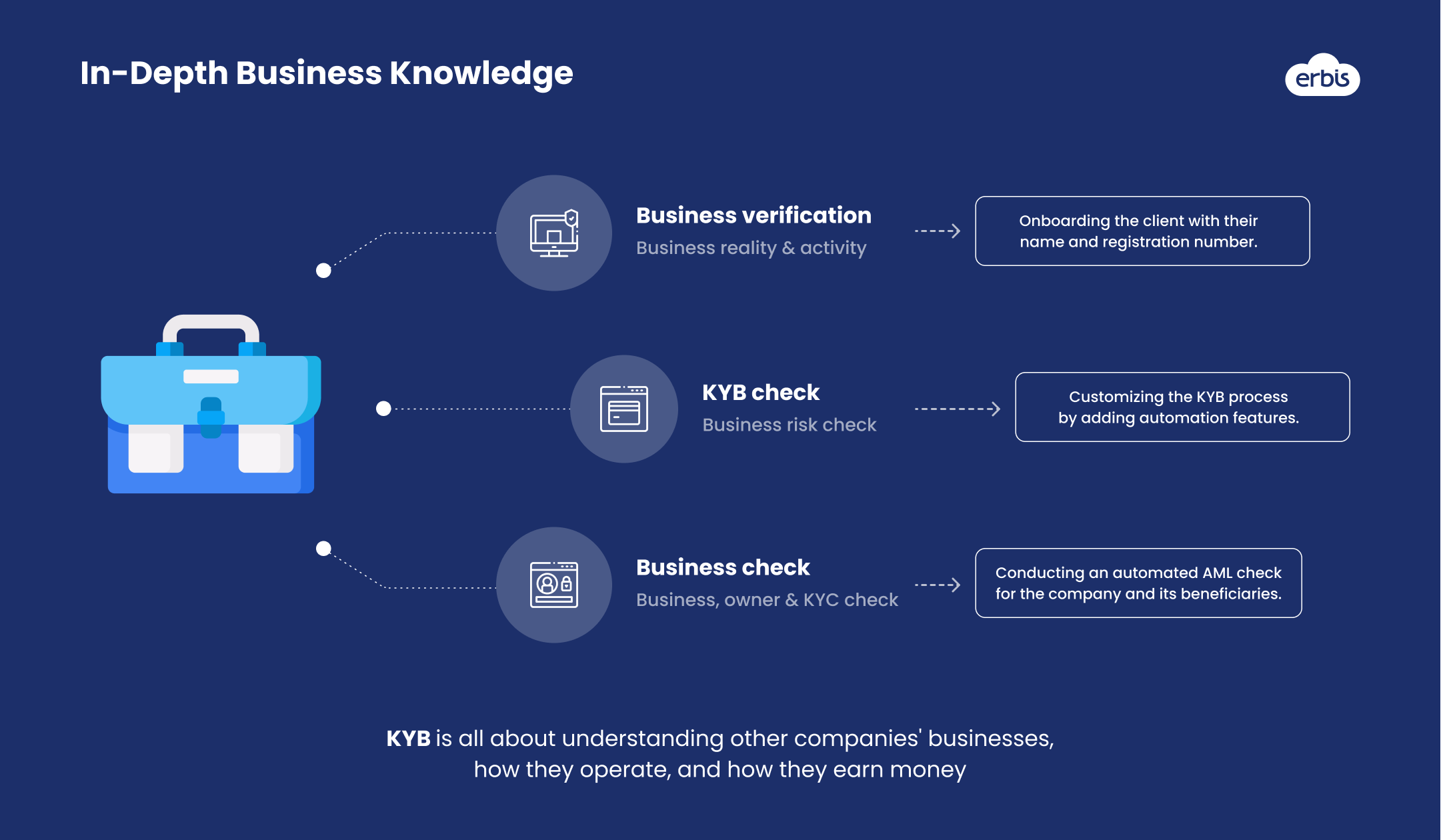
The KYB procedures can help you access adverse media, find out if the person has loan debt or problems with the law, and discover if they are considered a politically exposed person.
All in all, KYB is vital in confirming the reliability of business partners, whether they are organizations or individuals. It helps to reduce the risk of fraud, money laundering, and other illegal activities. Additionally, KYB procedures enable organizations to meet their legal and regulatory obligations.
Is KYB mandatory?
The short answer is yes.
In Europe, the KYB rules are introduced in the Fifth Money Laundering Directive (5AMLD). In the USA, the KYB requirements are outlined in Customer Due Diligence Requirements for Financial Institutions (CDD Final Rule).
5AMLD specifies KYB/KYC requirements for such entities as
banks
auditors
tax advisors
notaries
estate agents
gambling service providers
cryptocurrency exchanges
individuals who trade in goods that involve cash payments of €10,000 or more
Furthermore, any suspicions regarding money laundering/terrorism financing or doubts about the accuracy of prior due diligence efforts must be followed up by additional KYB procedures.
CDD Final Rule outlines the KYB requirements for the following organizations:
U.S. based banks
mutual funds
brokers or dealers in securities
futures commission merchants
introducing brokers in commodities
It requires these organizations to have written policies that are tailored to:
establish and verify the customers' identities
establish and verify the identity of the beneficial owners of companies’ starting accounts
comprehend the nature and goal of customer relationships for creating customer risk profiles
monitor activities to recognize and announce questionable transactions
While not all entities are obliged to implement KYB by law, all of them should consider it as a winning tool to establish transparent business relationships. By verifying identities through KYB, companies can reduce the risk of fraud, protect their data, and run legal-based operations.
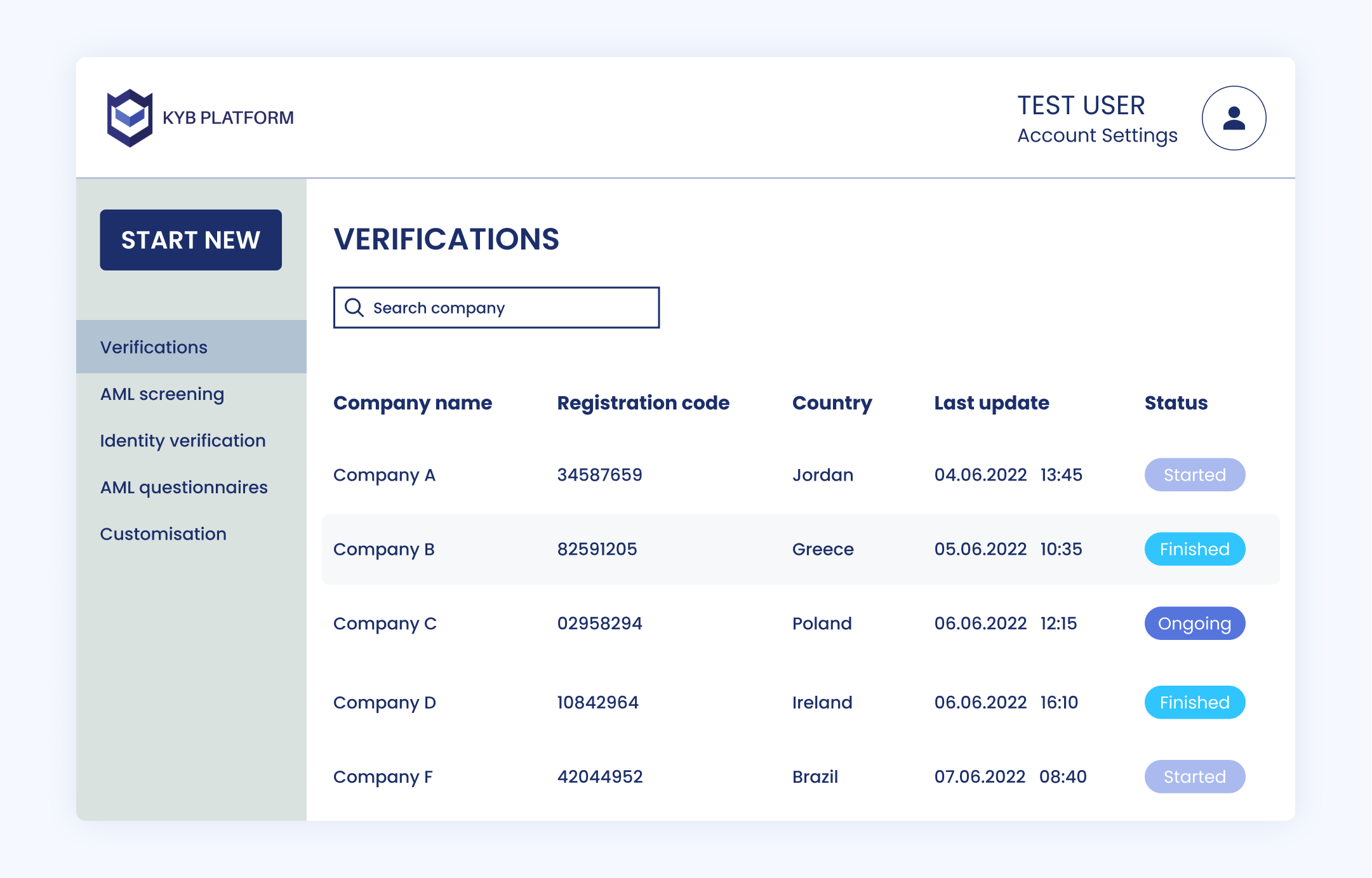
KYB checklist
CEOs and founders have a lot on their plate. They need to define the company's direction and vision, create goals and plans, and manage both operations and compliance with the law. Additionally, they need to nurture relationships with customers, suppliers, and other stakeholders. That's where KYB steps in. This strategy involves verifying data from potential partners against a variety of sources (e.g., government-issued documents, credit reports, financial records). For more clarification on what KYB should cover, our checklist provides some examples.
Essential company information. This typically includes such details as company name, address, contact information, date of incorporation, and ownership structure. Other information may be the company’s mission and vision statements, products or services offered and industry data.
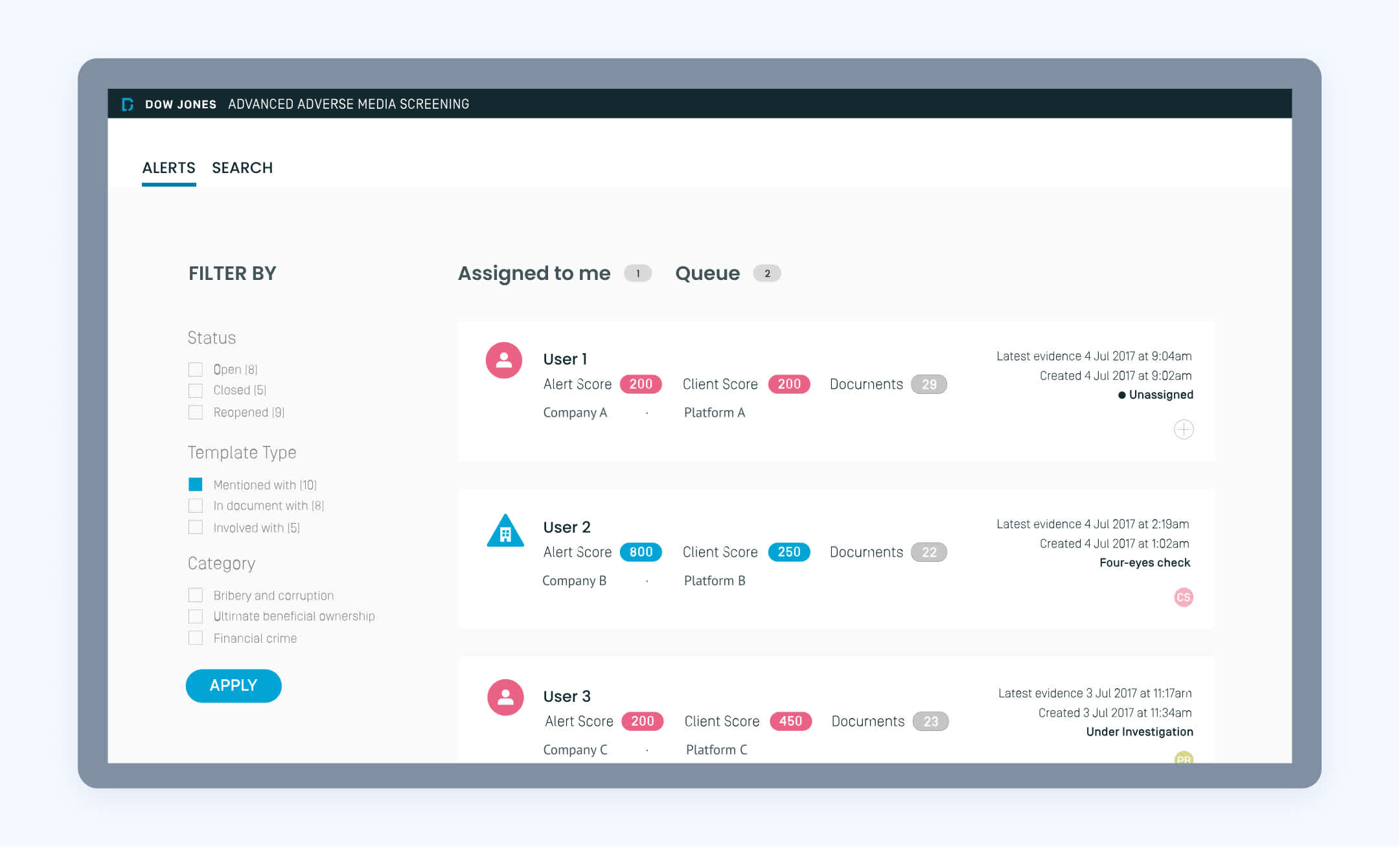
Sanction scanning. This is used to identify customers and transactions that may be subject to sanctions imposed by governments or other regulatory bodies. Sanction scanning involves searching through databases and other sources of publicly available information to identify people or entities that may be on a sanctions list.
Financial reports. These are documents that provide information about a company's financial standing, such as income, expenses, assets, liabilities, and cash flow. Additionally, they can provide information about the business' equity, debt, and liquidity.
Adverse media. This means screening various media resources to identify potential criminal activity, data breach cases, or any other negative information associated with a particular person or organization.
Legal compliance. This ensures that a company is adhering to all applicable local and international laws and industry-specific regulations. Compliance activities include maintaining records, filing taxes, following safety regulations, and adhering to anti-discrimination and anti-corruption laws.
Beneficiaries structure. This is a way of identifying who will benefit from the company's assets and income. It is typically established as part of a company's formation or restructuring process. The beneficiaries structure includes details such as who owns the company, who has control over it, who receives dividends, and who is entitled to receive the money from the sale of the company.

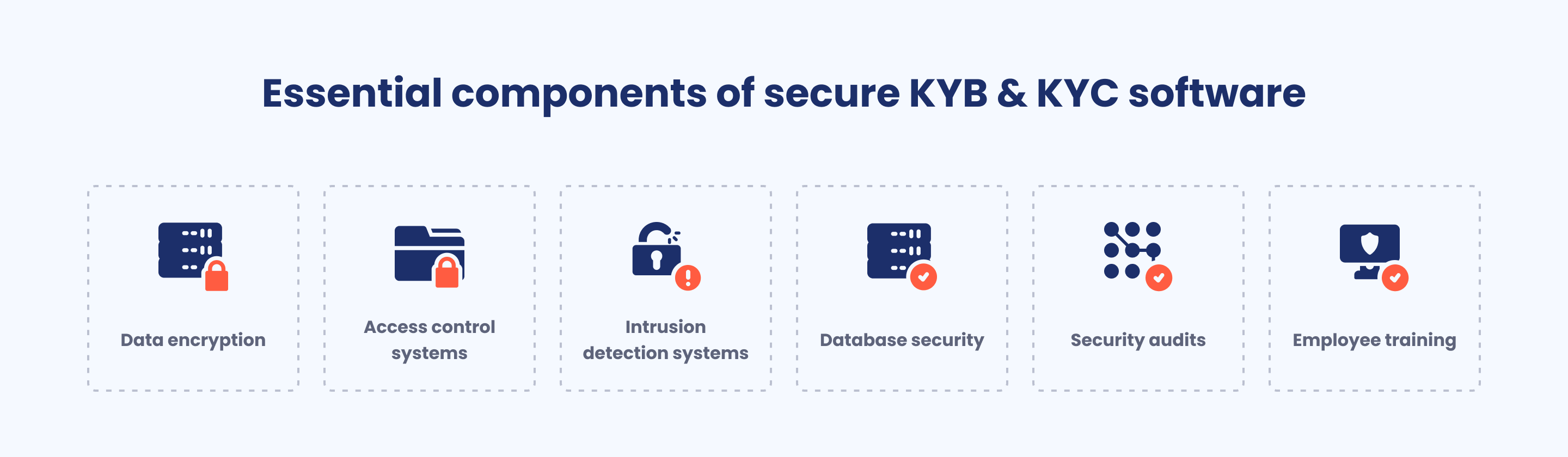
Security considerations for KYB & KYC software development
KYB & KYC software deals with sensitive information about individuals and organizations. It stores personal data related to finance, politics, and legal activities, which can be of interest to many malicious actors.
When developing KYB & KYC software, it’s crucial to pay attention to security. Here is what needs to be done.
Data encryption
You should encrypt data during acquisition, processing, and storage. For this, you should use
online cryptographic protocols, like SSL (Secure Sockets Layer) or TLS (Transport Layer Security)
hash algorithms like SHA-2 or SHA-3
data encryption algorithms like AES (Advanced Encryption Standard) and RSA (Rivest, Shamir, Adleman)
Access control systems
Develop access control systems to restrict the access of specific users to particular features or functions of your software. You can use the following access control types:
Role-based. You can create user roles such as administrator, accountant, security manager, etc. and provide them with access to specific functionality.
Attribute-based. You allow users who are, for example, type=employees and have department=Security to access the security check features.
Policy-based. This is similar to attribute-based access control but is more flexible. Policy-based access control can be updated dynamically and automatically (while attribute-based access control needs manual adjustment). For example, you could define a role for a manager and associate it with certain types of accounts on a server. Then, relevant users could be linked to this role.
Intrusion detection systems
In addition to access control systems, you may also use intrusion detection systems to help detect and mitigate any suspicious activity on your network. These systems use algorithms and data analytics to monitor any potential threats, alerting you if any suspicious activity is detected.
The intrusion detection systems can monitor the traffic from:
all devices on the network
independent hosts or devices on the network
protocol between a device and the server
application-specific protocols
Database security
You should select a secure database for your KYB & KYC software with multiple layers of protection. Here are the critical factors to consider:
Database location. The database should be located in a secure place and restrict unauthorized physical access to it. If your database is in the cloud, the cloud server provider will take care of it.
Access control. A minimum number of people should have access to the database. Full access is typically available only for database administrators. Other users have read-only access.
Activity monitoring. You should be aware of who and when accesses the database and how the data is being used.
Data encryption. The data in the database should be encrypted according to the latest encryption techniques.
Backing up. You should be able to retrieve data in case of an incident. The data copies must be protected as reliably as the database itself.
Security audits
The goal of a security audit is to identify software vulnerabilities. There are no specific algorithm for running the security audit, but, generally, you should adhere to the following stages:
Listing audit goals
Identifying assessment criteria
Identifying potential threats
Running security checks and pentesting
Assessing security policies
Assessing staff’s security awareness
Offering measures as for security system improvement
Employee training
The software development team working on the KYB & KYC software should understand the critical importance of data protection and have deep knowledge of security protocols and best practices. It is essential that the team follow a secure software development lifecycle and sign non-disclosure agreement before starting to work on the project.
Integrating with the latest technologies
When it comes to KYB and KYC, the most sophisticated solutions are based on Artificial Intelligence (AI), Machine Learning (ML), Data Science, and Deep Learning.
Smart algorithms allow the capturing of businesses' and individuals' profiles by quickly crunching massive amounts of data. They also provide intelligent insights when such information changes over time, allowing users to take proactive action to address potential risks.
Intelligent algorithms also identify a company's / an individual's behavior patterns and trends that can be leveraged to make more informed decisions. They can also uncover hidden data relationships that may have previously gone unnoticed, which helps optimize performance and identify new opportunities.
Simply put, AI, ML, Data Science, and Deep Learning are used in KYB to help you make better decisions for your business. The software can collect and analyze the necessary information in a matter of minutes. For comparison, such work, if done manually, takes from days to weeks or even months.
So, by using advanced technologies, you stay competitive in today's rapidly changing environment. Not only do you get access to the essential information but also save time and money leaving the tedious tasks to the machines.
Why Erbis for KYB and KYC?
At Erbis, we specialize in building secure, compliant technologies and systems that address KYB and KYC industry standards. We understand the value of speed and accuracy, which is why we have streamlined processes for quickly getting started and keeping project momentum going.
As a custom software development company, Erbis exists to help you develop the perfect solution for your business—no one-size-fits-all here! We take the time to understand your needs and create a tailored product that meets them exactly.
Our team works with a client from start to finish—from concept to deployment—to make sure everything goes smoothly and provide ongoing support once the project is complete. So, if you need the perfect KYB and KYC solution that will be in-demand across businesses, don't hesitate to get in touch.
