SSDLC: 7 Points to Check
According to the latest IBM report, the average cost of a data breach is USD $3.86 million. And we don’t take into account the company’s good name.
Secure Software Development Life Cycle (SSDLC) can help you significantly minimize the probability of data breaches and other security issues. It ensures in-depth testing at every stage of development and reduces the likelihood of security gaps. Below we will share the SSDLC best practices for custom construction software and discuss the steps and methods to make a secure app.
Why is secure SDLC so important for product owners and investors?
A secure SDLC is vital for many reasons: economic, legal, marketing, reputation, and so forth. Here is why owners should care about it:
Optimized costs
Sometimes, security is checked post-factum as a part of the testing strategy. This approach has proven to be inefficient because fixing bugs is much more expensive than preventing them. Obviously, adhering to the SDLC policy reduces potential risks and expenses.
Faster implementation
In terms of an SSDLC, the entire project is considered to be more concise. Since you are able to detect most security flaws along the way, you don’t have to spend extra time resolving bugs that become more complex by the end of the development.
Reliable software
A secure development model implies using architecture analyses, automation security code reviews, penetration tests, etc. Such activities help identify more vulnerabilities and create a reliable app system that is less sensitive to hacker attacks.
Legal compliance
Each country sets high software security demands. You must ensure that user data is protected and there is a low chance of data leak. A secure SDLC approach helps to ensure the product is safe during each phase of the development. It also provides legal grounds to launch the app.
Brand confidence
A stable app increases customer loyalty and stabilizes the brand’s position in the market. So when you invest in security, you are laying the foundation for a growing client base and your income.
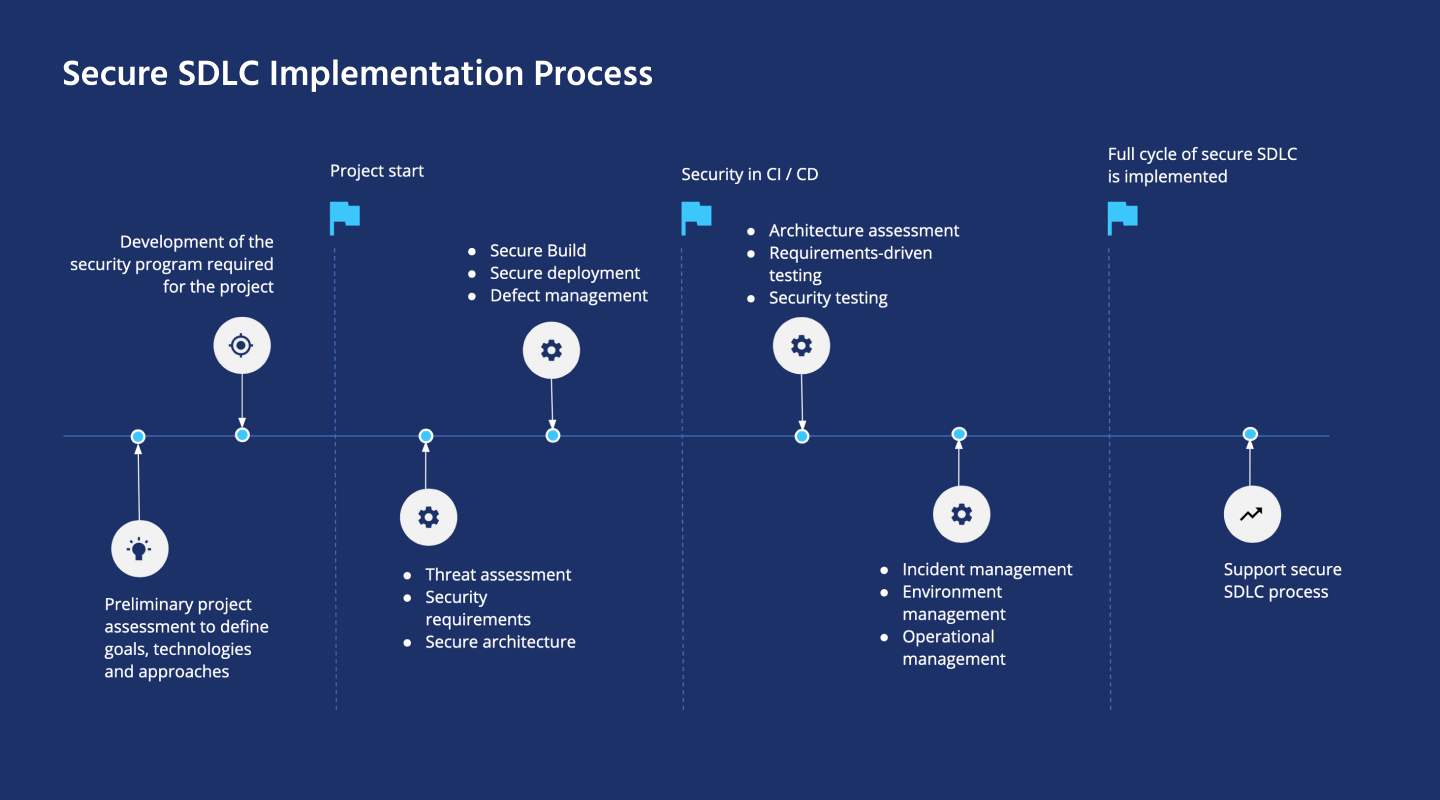
Five stages of the secure software development life cycle
Custom construction management software is a large-scale project preceded by deep analysis and careful planning. Secure SDLC steps are built with product specifics in mind, but in general, they look like this:
1. Plan
It covers business analysis, requirements capture, and cost assessment. Cybersecurity engineers work closely with stakeholders to draw a complete picture of the current business state and its goals. They assess the risks and provide a ROW development plan.
2. Create
It defines the development flow with emphasis on tech details. The final document at this stage describes:
app architecture
platforms range
programming languages
frameworks and utilities
security measures
3rd-party integrations
3. Develop
This is where the SSDLC implementation begins by following the plan designed earlier. The starting point is to check databases before the import of required data.
4. Test
The mandatory pre-release phase involves thorough testing that checks every nook and cranny of the app and proves its stability. Before getting to work, the QA team carefully studies the software requirements to understand the desired result. Next, they move to the head-to-toe scan, which involves unit testing, integration testing, acceptance testing, and non-functional testing.
5. Deploy
The last, but very important, step is deployment. Once you have deployed your app, there is a high probability of detecting new bugs. To solve them quickly you need a robust support system to catch any glitches and launch debugging. Thus, the end phase of the secure software development life cycle leads back to the first phase.
Secure SDLC checklist: what you should triple-check
We’ve covered the SDLC phases. Now let’s dig a little deeper and see what you need to check within the information security life cycle.
Security risks
You must know your enemies to win. So, start by evaluating risks and think of defensive measures for the most vulnerable points.
Security standards
They will help you understand what security level is acceptable for the software. Study legal regulations and also determine the individual rates that work for your app.
Architecture plans
Structural vulnerabilities carry huge risks to the app. That is why design schemes and architecture plans should be checked rigorously using threat model methods.
CI organization
With the CI model, developers often commit their code to the source code repository (usually once a day). Small changes help to quickly spot defects and take steps to solve them. That is why embedding CI is a vital step in the SDLC checklist.
Firmware reports
You can use automated tools to analyze firmware on a specific device. Although generated reports can give some information about primary and secondary gaps, cybersecurity specialists still have to double-check all the highlighted points.
System integrity
This is verified at the final stages of development. The goal is to ensure the system meets the business, functional, and technical requirements set during the planning phase.
Live environment
Checking security in SDLC doesn’t end with a software release. Although pure coding may be paused here, you need to constantly monitor the app’s behavior and make changes in time if something goes wrong.
Who can implement security in SDLC correctly?
Secure SDLC should be put under the care of security developers. They have vast experience in cybersecurity engineering and network security fields. Such specialists regularly take special courses and can boast certificates from reputable software vendors.
There is no way to become a security developer shortly after graduation because such a specialty does not exist. This status may be obtained with strong expertise in software engineering that comes after several years of work with complex products.
Summing Up
The secure SDLC standards help achieve better performance, reduce possible expenses, and increase product value. It forces you to check every step during project development making sure no critical bugs exist. Adhering to secure dev practices is an absolute must for apps that work with user data and take care of essential processes of business. Custom construction software is all about that. So, if you want to make it, consider taking the secure SDLC plan on board. While blindly following the plan gives no guarantees, wisely adhering to it provides a higher likelihood of achieving great results.

