KYC Software Development: What Do You Need to Know in 2024?
KYC, or Know Your Customer, is the process of verifying a customer's identity and gathering information about them.
As the world becomes more digitized, online scammers are mastering their skills, and cybercriminals are using more sophisticated methods to access sensitive data. Given this, KYC software is quickly becoming an essential part of doing business. Not only does it help to verify customer identity, but it also monitors transactions for suspicious activity, fights money laundering, and counters the financing of terrorism.
In this article, we'll take a look at the latest trends and technologies in Know Your Customer software development. We'll also discuss how you can prepare for these changes and stay ahead of the curve in 2024 and beyond.
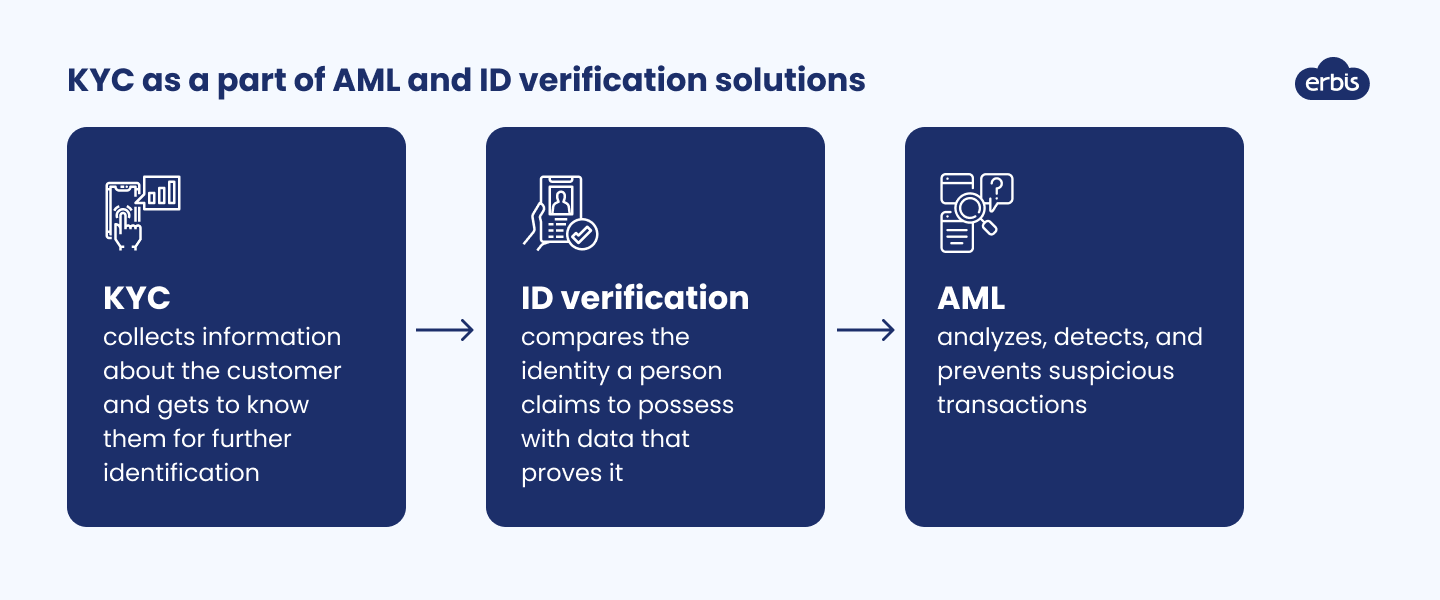
KYC as a part of AML and ID verification solutions
The notions of KYC, AML, and ID verification are often used interchangeably. Yet, even though these concepts are similar, they are not the same.
KYC
You are likely aware of the process of opening a bank account, which requires you to provide identity documents that confirm you are who you say you are.
This is what KYC is about. Its main goal is to collect information about the customer and get to know them for further identification.
KYC software solutions for banks and other financial institutions automate collecting information about the client. They allow customers to upload documents in electronic format and enable organizations to extract data using specially developed KYC protocols and data processing tools.
ID verification
ID verification aims to compare the identity a person claims to possess with data that proves it. For example, when you buy from an online store, the bank asks you to confirm the purchase in a mobile banking application. In order to do this, you need to enter a unique password or log in using biometrics. Thus, you verify your identity and give the bank approval to conduct a transaction.
ID verification tools are used not only in banking but also in fields such as insurance, healthcare, e-commerce, education, communication, and more. With the help of ID check software, enterprises reduce fraudulent transactions, build more trustful relations with customers, and personalize marketing campaigns.
AML
AML(anti-money laundering)is the procedure of detecting and preventing suspicious transactions. For example, if your daily spending hasn't ever exceeded $50 and you're trying to make a multi-thousand-dollar purchase, a bank will not authorize the transaction until they are convinced of your identity.
AML software solutions are increasingly used by financial organizations to analyze the spending habits and purchasing patterns of customers, as well as model their financial behavior. The implementation of AML tools is an important part of a company's BPA (business process automation) process. It allows you to rationally distribute the load between human operators and machine algorithms and receive timely warnings about any attempted fraud.
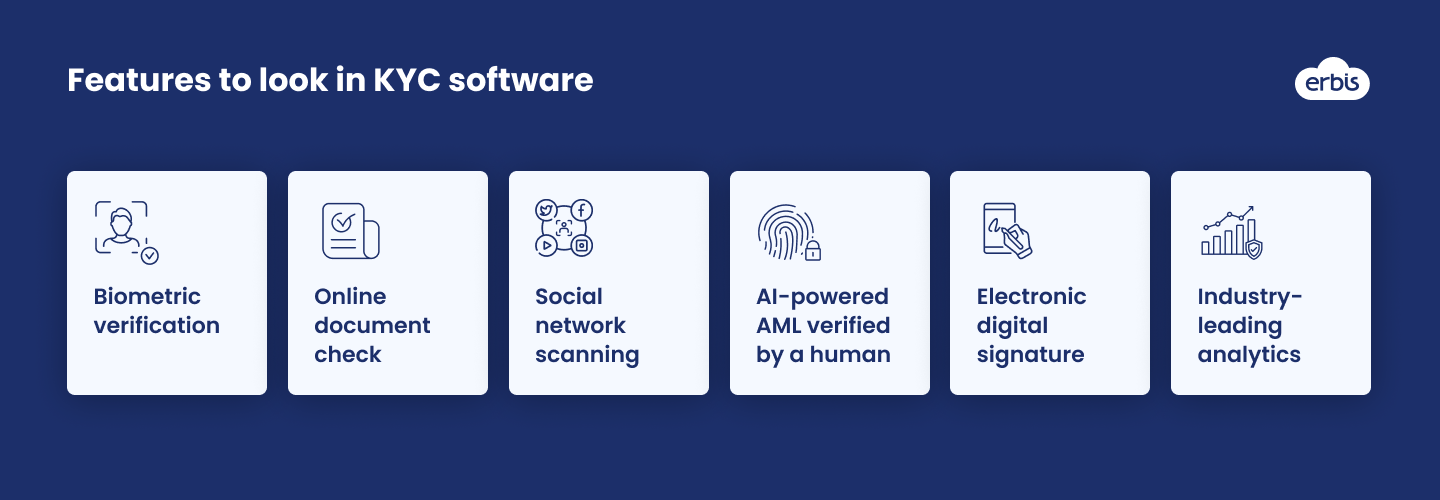
Most popular KYC features and services so far
You need to be aware of the most popular KYC services and features if you're planning to develop KYC software.
Biometric verification. This feature in KYC software uses unique physical characteristics to identify individuals. This could be anything from fingerprints to DNA profiling. Device sensors read the unique data of a person and eliminate the possibility of third parties accessing user bank accounts.
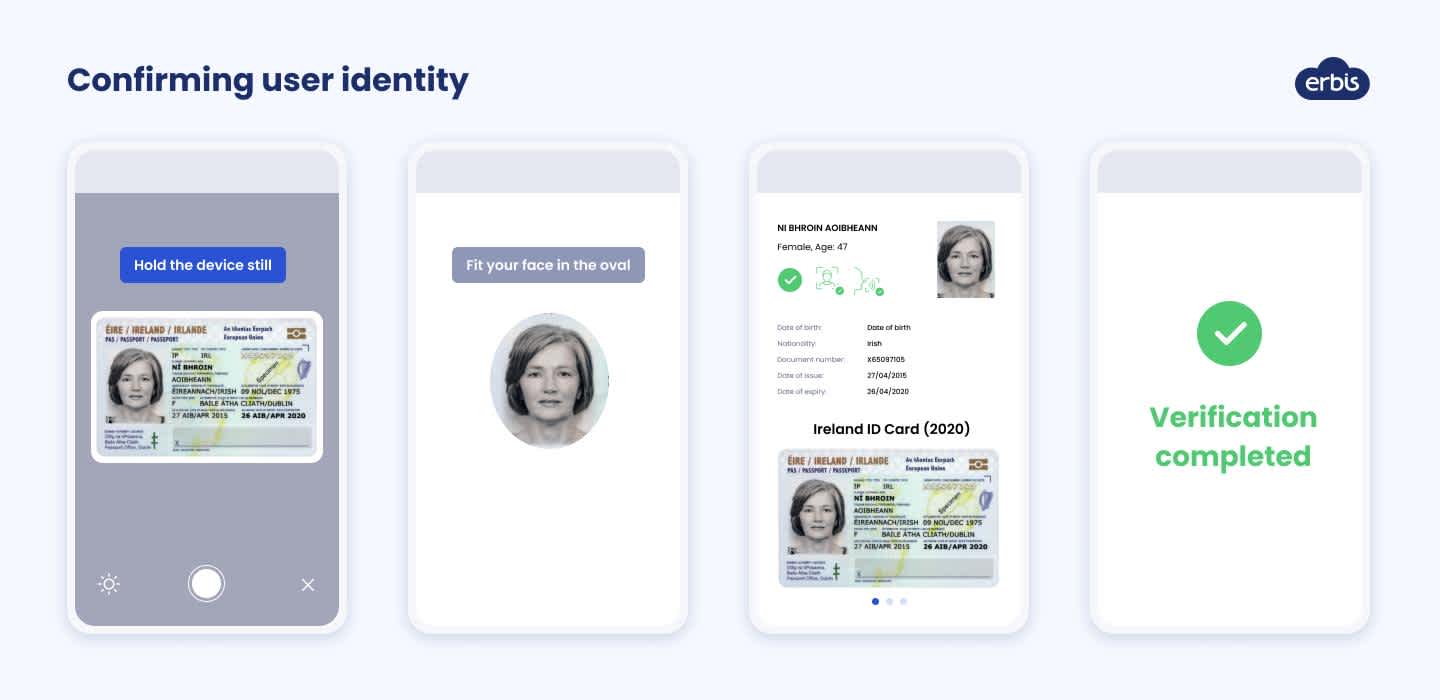
Online document check. This allows organizations to verify the identity of an individual by comparing their details with data held on a third-party database. For example, when a user uploads a photo of a passport or tax ID, KYC software can check if their name, age, date of birth, etc. matches the person in the registration account of a certain region.
Document owner verification. Even if a user has uploaded legal documents to the system, you cannot be sure that those documents belong to them. Using computer vision technology in your ID verification software, you can match a selfie taken with a phone camera with a photo in a document and verify the user's identity.
Social network scanning. Social media have long evolved from an entertainment tool to a valuable source of information about a person. Your KYC software can connect to different social platforms and analyze users' comments, reposts, and interests. If you identify alarming activities, you can refuse further cooperation.
AI-powered AML verified by a human. You can significantly reduce costs by trusting artificial intelligence to analyze suspicious transactions. However, some human participation is advisable in order to minimize false positives and customer dissatisfaction. You can let AML scanners built into your KYC software do the initial analysis but leave the human managers to make the final decision on classifying a case as fraudulent.
Electronic digital signature (EDS). A digital signature is created by using cryptography to transform electronic data. It is generated with a private key and verified with a public key. Using EDS in KYC software ensures the integrity of customer data, identifies the signatory, and gives legal force to all the documents. EDS can greatly simplify document flow within your organization and expedite transactions with external parties.
Industry-leading analytics. KYC software should not only protect you from scammers but also provide a report on the work done. Deep analytics, which shows the number of detected criminals, prevented cases of theft, unrecognized fraudulent transactions, and false positives, helps evaluate business and software effectiveness. Thus, using KYC reporting tools, you can detect weak points in your business processes and focus your efforts on eliminating them.
Benefits of custom KYC software development
When it comes to KYC software, you can choose a pre-built tool or develop a custom solution tailored to your specific needs. Both options have their benefits, but custom software development is the clear winner for companies that value time and money and aim for business growth.
To create an effective custom KYC software solution, you need to develop a detailed software requirements specification. It will help all stakeholders agree regarding functional and non-functional requirements, selected technologies, and team composition.
Here are the main benefits from custom KYC software development:
1. You'll get a solution fully adapted to your business processes.
2. You'll have full control over your data.
3. You'll be able to scale up quickly and easily.
4. You'll be able to quickly respond to customer needs.
5. You'll not have to depend on a third party.
6. You'll have the right of ownership of your software.
7. You can sell your software to other businesses and generate revenue.
Emerging technologies in KYC software development
There's no doubt that KYC software development is going to change greatly in the next few years. Companies will adopt advanced technologies and methods to secure their businesses and make customer interactions more personalized.
Here are some of the KYC trends and technologies to keep an eye on:
Artificial intelligence. KYC software will soon be able to automate many of the manual tasks currently done by humans. Not only will AI undertake repetitive, simple duties, but it will also be able to make more informed decisions in non-standard situations. The main advantages of AI over humans are anti-bias assessment, 24/7 work, and stable productivity. Given that humans make up to 50 errors per working shift, AI could soon become a worthy replacement as it constantly develops and evolves.
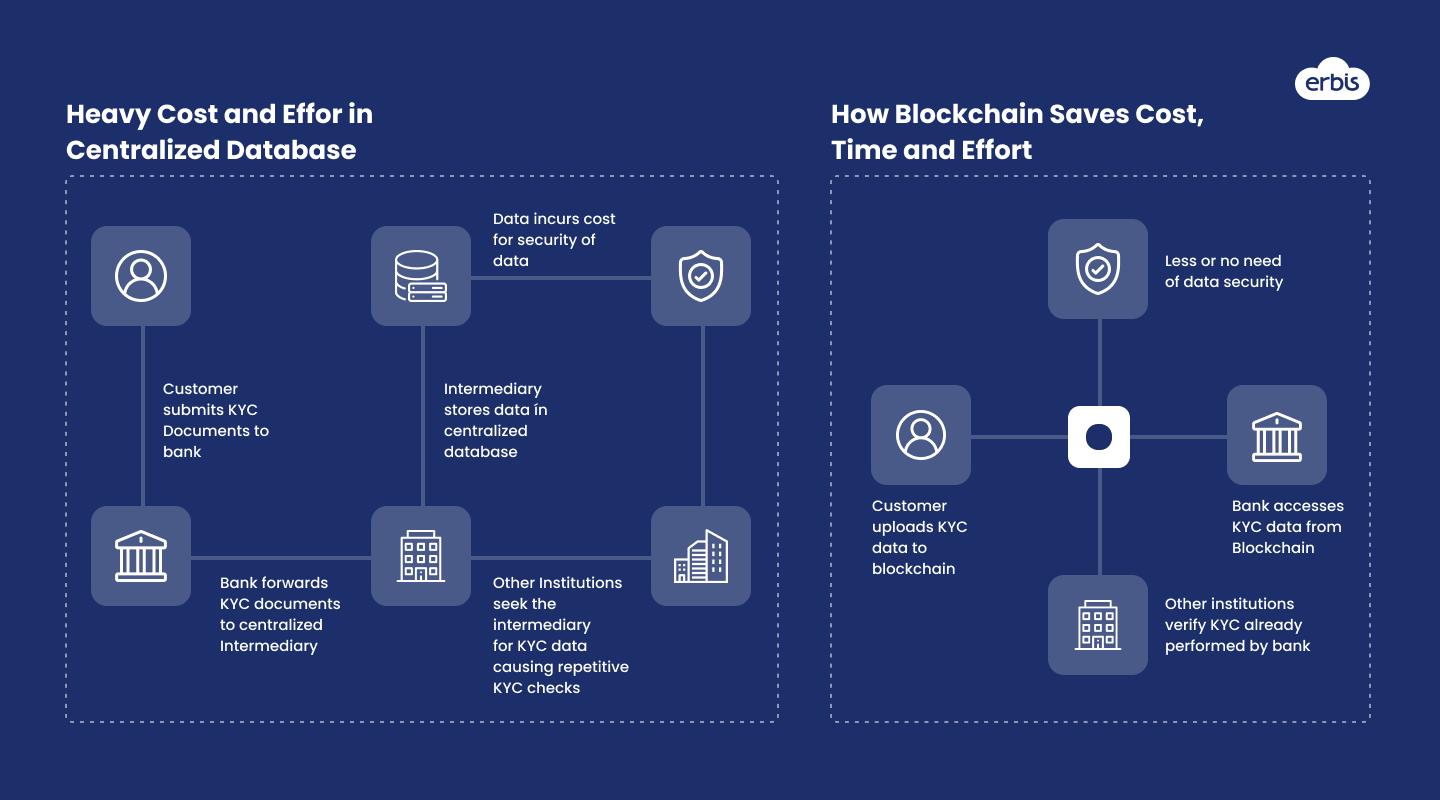
Blockchain. KYC software powered by blockchain has the potential to significantly reduce the time required for data processing. Financial institutions can enter customer data into the distributed ledger, which can then be accessed by other institutions to reduce waiting times for customers. However, it's important to note that third-party access to customer data is only possible with the customer's consent.
Cloud computing. The cloud is already making a big impact on AML and KYC software development. In upcoming years, it's only going to get bigger. Cloud-based solutions are more secure, scalable, and cost-effective than traditional software, so expect to see more companies move their KYC and AML transaction monitoring to the cloud.
KYC compliance challenges and solutions
Despite its significant benefits, implementing KYC software comes with specific challenges. Understanding and addressing these challenges is crucial for successful KYC compliance. Below are common KYC software development challenges and solutions to overcome them:
Data privacy and security concerns. Storing sensitive customer data can pose significant risks to privacy breaches and cyberattacks. You should take the necessary steps to ensure the security of such data during the KYC software development. Particularly, you should encrypt data during the transition and at rest, implement secure data storage, and comply with relevant data protection regulations such as GDPR or CCPA.
Regulatory compliance complexity. KYC regulations vary across jurisdictions and are subject to frequent updates. To maintain compliance with these regulations, you should continuously monitor changes and update KYC processes accordingly. A centralized compliance management system can help you streamline this process and guarantee compliance with regulatory requirements.
Cost considerations. Developing KYC software involves significant costs associated with software licensing, infrastructure setup, and ongoing maintenance. Before starting the development process, it is crucial to conduct a cost-benefit analysis to determine the points where the expenses will be incurred and ways to monetize the KYC software.
How do I get started with KYC software development?
If you want to automate KYC with the help of software technologies here are the steps to follow:
Understand the customer data you need to collect
Study the legal framework that regulates data access in the target region
Define the KYC processes you want to automate
Outline KYC software features
Discuss the technical part of KYC software development with IT experts
Agree on the cost and deadlines of KYC software development
Develop and launch KYC software
If you need help with ID verification and KYC software development, feel free to contact our team. All you need to do is fill out our quick and easy online form. Once you've submitted your information, one of our managers will be in touch to schedule a consultation.
We'll go over your company's requirements and map out a plan that best suits your needs. We want to make sure that KYC software developed by our team is a perfect fit for your business, so we take the time to get to know you and your company inside and out.

