Mastering Security Challenges in Cloud Migration: An In-Depth Guide by Erbis
As more businesses embrace the benefits of cloud computing, the process of migrating to the cloud has become increasingly prevalent. However, amidst the excitement of enhanced scalability and flexibility, it is crucial not to overlook the critical aspect of security.
Modern cloud providers use advanced tools and methods to protect their clients' data and minimize security risks. Even so, much of the responsibility still rests with the client. So, if you decide to move your software system to a third-party IT infrastructure, you must take steps to ensure cloud migration security and mitigate potential cybersecurity threats.
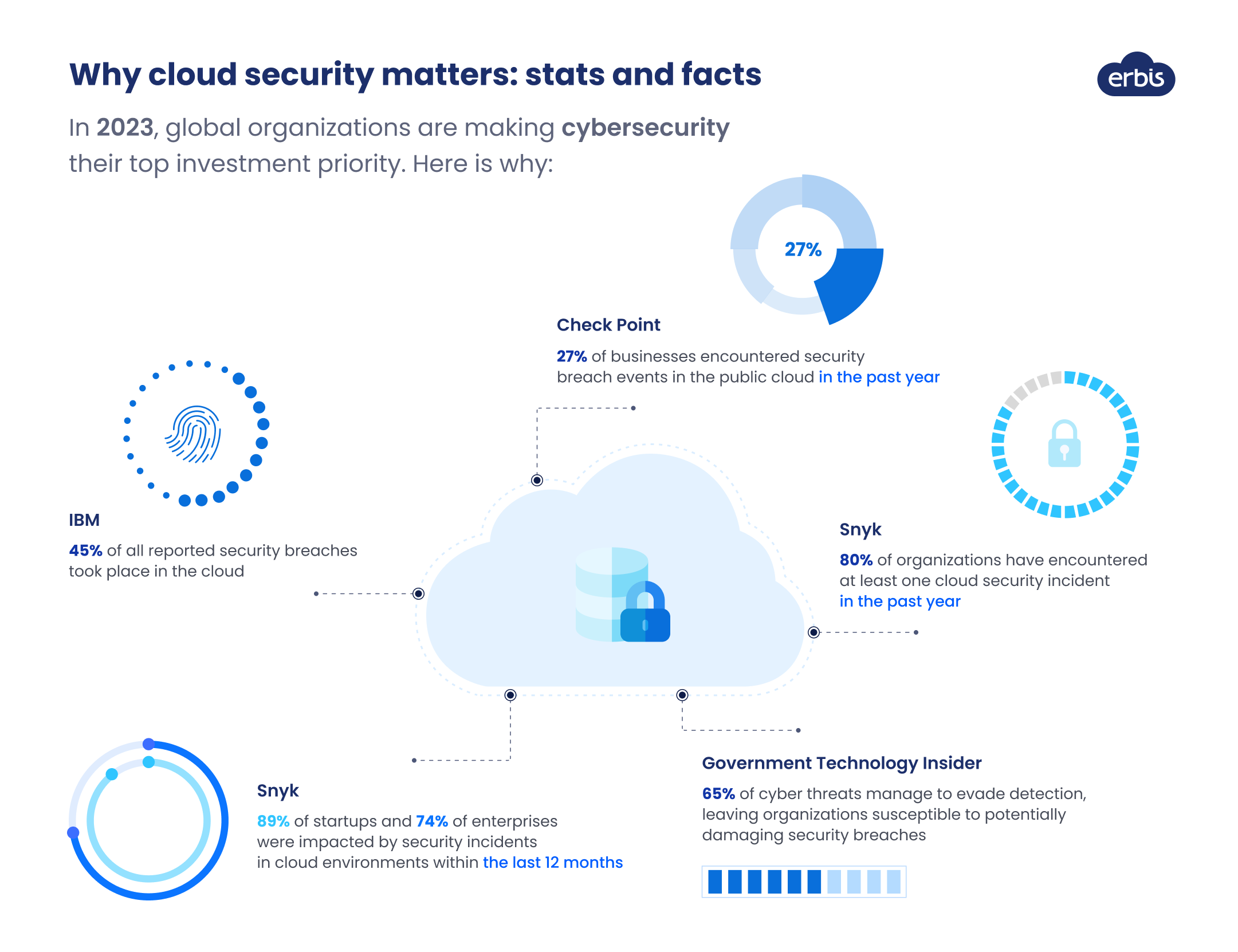
Why cloud security matters: stats and facts
In 2023, global organizations are making cybersecurity their top investment priority. Here is why:
45% of all reported security breaches took place in the cloud (IBM)
80% of organizations have encountered at least one cloud security incident in the past year (Snyk)
27% of businesses encountered security breach events in the public cloud in the past year (Check Point)
89% of startups and 74% of enterprises were impacted by security incidents in cloud environments within the last 12 months (Snyk)
65% of cyber threats manage to evade detection, leaving organizations susceptible to potentially damaging security breaches (Government Technology Insider)
Cloud migration security: tackling challenges and implementing solutions
Despite cloud migration security concerns, organizations are increasingly using cloud technologies. According to Google, 41,4% of companies are planning to increase their investment in cloud-based services. This is not surprising because cloud infrastructure benefits businesses in many ways, providing them with:
effortless and fast scalability
quick access to advanced IT tools
flexibility in managing IT resources
However, to get the most out of the cloud environment, you need to secure your infrastructure and address cloud migration security concerns.
Challenge #1: Data breach
A leak of sensitive data is a significant concern during cloud migration. To address this, you can:
Implement strong access controls: use role-based, attribute-based, or policy-based access control systems to ensure only authorized individuals can access specific data
Encrypt data: apply encryption techniques to protect data at rest and in transit; use online cryptographic protocols, like SSL or TLS, hash algorithms like SHA-2 or SHA-3, and data encryption algorithms like AES and RSA
Choose reputable cloud service providers (CSPs): select CSPs with a proven track record of strong security measures and compliance certifications.
Challenge #2: Data loss
Cloud migration can lead to data loss due to accidental deletion, software bugs, or hardware failures. You can mitigate this risk by taking the following steps:
Backup data: create a database copy on your old server before transferring data to the new one; after migration, establish a backup strategy that includes frequent backups and redundancy across multiple cloud regions or providers
Test backup and restore procedures: regularly verify the integrity of backups by testing the restoration process
Create a disaster recovery plan: outline and test steps to recover data in case of a catastrophic event
Challenge #3: Compliance and regulatory issues
Moving sensitive data to the cloud requires compliance with relevant regulations (e.g., GDPR, HIPAA). Address this concern in the following ways:
Understand regulatory requirements: familiarize yourself with the specific regulations that apply to your industry and the data you handle.
Evaluate CSP compliance: Ensure your chosen CSP adheres to necessary compliance standards and provides relevant certifications.
Implement proper data governance: establish appropriate data access controls, monitoring mechanisms, and audit trails to ensure compliance with regulations
Challenge #4: Account hijacking
Unauthorized individuals gaining control over cloud accounts can lead to data breaches or service disruptions. You can prevent this by taking the following steps:
Enforce strong passwords and MFA: encourage users to create complex passwords and enable MFA to add an extra layer of security
Monitor abnormal activity: implement security monitoring tools that identify suspicious activities or unauthorized access attempts
Limit privileges: grant user access with the principle of least privilege, ensuring users have only the necessary permissions to perform their tasks
Challenge #4: Cloud provider vulnerabilities
Even reputable CSPs can have vulnerabilities, potentially exposing your data. To address this:
Stay updated on security patches: regularly update and patch your systems to protect against known vulnerabilities
Perform third-party audits: conduct security audits or assessments of your CSP's infrastructure and processes to ensure they meet security standards
Implement network security controls: employ firewalls, intrusion detection systems (IDS), and other security measures to protect your cloud environment
Challenge #5: Data governance and ownership
Clarify data ownership and control to prevent any disputes or unauthorized use. Steps to take include:
Define data ownership policies: establish ownership and usage rights for data stored in the cloud
Review service level agreements (SLAs): ensure the SLA with your CSP addresses data ownership, confidentiality, and data protection requirements
Retain data control: maintain administrative access and control over your data, even when stored in the cloud
Challenge #6: Virtual machine setup
Improperly configured VM settings, such as open ports, default credentials, or unnecessary services, can create security vulnerabilities. It is crucial to follow security best practices and harden the VM configuration. Here is what you can do:
Regularly update the VM: enable automatic updates or establish a process to promptly apply security patches
Configure secure network: set up firewalls, restrict access to specific ports and protocols, and disable unused services
Enable logging and monitoring: monitor logs for suspicious activities and set up alerts for potential security incidents
Challenge #7: Application Programming Interface (API) management
APIs provide the means to extract, transform, and load (ETL) data from source systems to the cloud environment. To ensure data integrity and consistency during the migration process, you can do the following:
Implement strong authentication protocols: use API keys, tokens, or OAuth to prevent unauthorized access to sensitive data
Use secure communication protocols: these include HTTPS (Hypertext Transfer Protocol Secure), SSH (Secure Shell), SFTP (Secure File Transfer Protocol), and others
Vet third-party APIs: assess their security measures, data handling policies, and compliance with security standards
Challenge #8: Complicated pricing
Cloud service pricing is often confusing and non-transparent. To calculate a precise figure, you can do the following:
Use official pricing calculators: you can find them on the official websites of cloud providers. Here are the links to AWS, Microsoft Azure, and Google Cloud calculators
Take specialized courses: sometimes pricing models are so complicated that you need to enroll in a price-educational course to understand them
Cooperate with a cloud migration specialist: with expert help from companies like Erbis, you can rest assured you pay a fair price for the resources you need

Cloud migration plan as a powerful security measure
Cloud migration security largely depends on how consistently the transitioning process is planned. Taking cloud migration as a serious business decision, you can carefully prepare for it and make sure your data transfer proceeds without unexpected issues.
Below we provide an example of a cloud migration plan that ensures the security and consistency of the project:
1. Define objectives
Clearly articulate the goals and expected outcomes of the cloud migration. Do you want to improve scalability, reduce costs, or enhance disaster recovery capabilities? Whatever your objectives are, they must be represented in quantitative and qualitative terms. For example, you may set a goal to increase application response time by 20% or reduce infrastructure costs by 30% within the first year of cloud migration.
2. Assess current infrastructure and requirements
Evaluate the existing on-premises infrastructure, including hardware, software, and network architecture, to understand your system's technical requirements and dependencies.
Identify any potential compatibility issues or constraints that may arise during the migration process.
Determine the necessary resources and support required for the cloud migration.
3. Select a cloud service provider
Research and select a CSP that aligns with your organization's needs, considering factors such as data security, compliance certifications, performance, pricing, and availability.
According to the recent Gartner report, the leading cloud providers are AWS, Microsoft, and Google. You can start by exploring their features, tools, and pricing models to decide which CSP fits your requirements best.
4. Plan migration strategy
Define the migration strategy based on your business goals and needs. You can use one or a combination of the following approaches:
Lift and Shift. Move the software system as-is to the cloud without making significant changes.
Rehosting. Migrate the system with minimal modifications to utilize cloud infrastructure.
Refactoring. Restructure the software system to leverage cloud-native services and optimize performance and scalability.
Rebuilding. Rebuild the ERP system from scratch using cloud-native technologies and services.
5. Securely migrate data, applications, storage, and network
Use bulk migration, incremental sync, or a hybrid approach to transfer your software system from on-premises to a cloud-based environment.
Take care of cloud migration security by
establishing identity and access management controls
enabling strong data encryption
implementing firewalls, intrusion detection systems, and logging mechanisms
ensuring compliance with relevant regulations and standards
6. Test and validate your software on a new cloud environment
To ensure your software operates as expected, perform rigorous testing and QA procedures:
test core functionalities, workflows, and integrations
perform load testing and performance tuning
validate data consistency and accuracy between the on-premises and cloud environments
7. Train staff and manage changes
Prepare the team to maintain software on the cloud platform. Implement comprehensive change management and education strategy, provide necessary documentation and resources, and address any concerns or challenges related to cloud migration.
Multi-cloud as a part of security strategy
Multi-cloud means using multiple cloud service providers simultaneously. With a multi-cloud approach, you can store data on different cloud servers, and thus be less dependent on a single third-party organization. Multi-cloud is also used for keeping backup instances outside the main IT infrastructure. This allows you to quickly recover the system in case of an emergency on the primary provider's side.
Multi-cloud is a workable way to set an extra security layer for your cloud-based product. It also provides flexibility in selecting best-of-breed security solutions from different providers and leveraging cloud providers with specific certifications or geographical coverage.
However, managing security in a multi-cloud environment requires careful planning, consistent security policies, and centralized monitoring. You will need the help of experienced DevSecOps to implement incident response capabilities across all cloud platforms and ensure your data is well protected across the servers.
Sharing security responsibility
Cloud migration is a wise move for organizations looking for scalability, flexibility, and security enhancement. Modern cloud providers understand the necessity of data protection, which is why they use advanced security tools and approaches to save clients from hacker attacks and data breaches. However, it is a mistake to think that migrating to the cloud frees you from security management and responsibility. While cloud providers offer robust security measures, organizations still have a crucial role in managing and maintaining the security of their cloud environment.
Moreover, the shared responsibility model clearly delineates the responsibilities of the provider and the customer. As a rule, it specifies that the provider is responsible for the security of the cloud, while the customer is responsible for the security within the cloud.
Below, you can see the AWS shared responsibility model outlining the amount of configuration work you must perform as part of your security responsibilities.

Cloud migration security with Erbis
At Erbis, we've been providing cloud migration and cloud development services for 11 years. We've helped numerous clients to move their products into cloud environments and achieve great scalability and flexibility with cutting-edge cloud technologies.
Our expertise spreads to migrating software systems from on-premises to cloud infrastructures, implementing cloud-to-cloud transitioning, developing cloud-based products, and modernizing legacy systems on the selected cloud platforms.
To learn more about our expertise, check out our recent cloud-based projects:
Re-architecting cloud structure for a marketing SaaS provider ➟ read full story
Creating a cloud-based strain database for collaborative lab research ➟ read full story
Developing a cloud-based construction management solution ➟ read full story
If you need expert help in cloud migration security, don't hesitate to get in touch.
