Cybersecurity Solutions and Services
Your data safety is our business
Protect your operations, critical assets, and infrastructures from threats and breaches. Implement the best cybersecurity practices relying on our proven expert competence and long-standing software development background.
What We Do
From initial security assessments to full-scale security implementation, we guide you through every stage, ensuring robust digital protection that aligns with your strategic risk management objectives.

Our expert team provides comprehensive cybersecurity services:
- Cybersecurity Audit We conduct comprehensive security assessments of your IT infrastructure to uncover vulnerabilities before they become threats, prioritize improvements, and ensure regulatory compliance.
- Strategic Cybersecurity Consulting We develop and implement customized security strategies aligned with your business objectives, incorporating advanced protection measures that evolve with emerging threats.
- Secure Development Lifecycle We integrate security throughout your software development process with automated testing and DevSecOps practices to ensure your applications are resilient against cyber threats from day one.
- Information Security Models We design and implement multi-layered information security frameworks that protect your sensitive data through robust access controls, encryption, and data loss prevention.
- AI Security We ensure your artificial intelligence and machine learning platforms, models and applications are ethical, secure and compliant with regulations while protecting against potential threats and data breaches.
- Cloud & Network Security We implement tailored cloud security and network security solutions with zero-trust architecture, next generation firewalls, and intrusion detection systems to secure both cloud-based and on-premises infrastructure.
We Are Ready to Share Our Experience
12years of experience
100+engineers
$110Moptimized costs
95% customer satisfaction rate
Why Choose Erbis
Flexibility guided by the goals and needs of our client
Changing requirements is welcomed, even late in the development. We also offer a model that gives you complete freedom to scale the project on the go.
Top talents
We engage only senior-level experts, constantly perfecting their skills. This ensures we deliver the best possible custom mobile solutions to save you time and money.
Speed
Our clients can see the progress regularly. Should you decide to give us an assignment today, we’ll have something to show you in as little as 2 weeks!
Comprehensive software product development across all platforms
We can resolve tech challenges of any complexity, from the development of custom solutions to the most complex integrations and implementations.
DevOps culture
We build DevOps processes that can ensure 99,999% uptime. Our striving for high reliability goes beyond tools: it's about systems ready for any challenge.
Cutting-Edge AI & ML Integration
We adopt the latest innovations in the industry to provide the most suitable artificial intelligence and machine learning services for our clients.
How We Work with Cybersecurity Implementation
A comprehensive cybersecurity strategy helps prevent digital vulnerabilities, protects critical assets, and minimizes potential financial and reputational risks. At Erbis, we have a refined methodology for transforming your digital security landscape.
Whether you need a complete security ‘posture overhaul or targeted vulnerability management, we'll ensure implementation is thorough, precise, and strategically aligned with your business objectives:
1. Assessment
Our team will conduct an in-depth security diagnostics of your current digital infrastructure, network architecture, and data protection mechanisms to identify potential vulnerabilities and determine your specific security requirements.
2. Strategic Planning
We will develop a customized cybersecurity roadmap, selecting the most appropriate defense technologies and frameworks tailored to your organizational risk profile. Our approach includes comprehensive threat modeling and proactive risk mitigation strategies.
3. Preparation
Before implementing security solutions, we'll ensure your digital ecosystem is optimized, conducting thorough baseline security audits and preparing your infrastructure for advanced protective measures.
4. Implementation
Our expert security engineers will deploy multi-layered defense mechanisms, integrating cutting-edge protection technologies across your network, cloud, and endpoint environments with minimal operational disruption.
Validation
We conduct rigorous penetration testing and security simulations to verify the effectiveness of implemented security measures, ensuring robust protection against potential cyber threats.
Continuous Support
We provide ongoing cybersecurity monitoring, delivering prompt incident response, regular security updates, and proactive threat intelligence to maintain your digital resilience in an ever-evolving threat landscape.
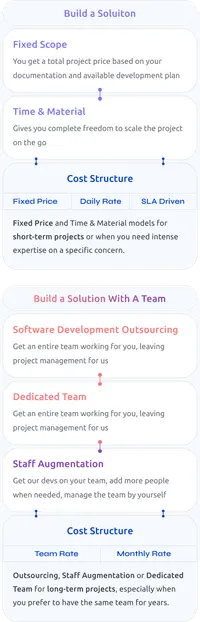
Models of Cooperation
We offer flexible cooperation models tailored to your specific needs, allowing us to align our services with your timeline, resources, and goals. Whether you need staff augmentation, outsourcing, dedicated teams, or other options – the choice is yours.
Our Process
STEP ONE
Share your challenges
We begin with a discovery call to understand your needs. We exchange documents and execute an NDA. We'll discuss your requirements, team structure, success criteria, business objectives, and timelines to identify how we can bring maximum value.
STEP TWO
Get a detailed solution
Within a few days, we’ll analyze your requirements, finalize project specifications, and agree on an engagement model and team structure. You’ll receive a proposal featuring a clear roadmap and our technical assessment, with thought-out insights from our experts—real value without obligations.
STEP THREE
Expect first deliverables
Upon contract signing, we’ll start working on the project immediately. In the case of development, we’ll have something ready for you in as little as 2 weeks! We’ll track performance, provide weekly or monthly updates, and continually adapt to your evolving needs.
In the case of consulting, we cooperate one-on-one or hold team meetings, deliver the roadmap, help execute the proposed strategy, and optimize and scale operations.
Tech Stack

AWS

Microsoft Azure

Google Cloud

Digital Ocean

PostgreSQL

MySQl

MSSQL

DynamoDB

MariaDB

Amazon Aurora

MongoDB

Redis

RedShift

ClickHouse

React.js

Angular

NextJS

Vue.js

Svelte.js

OpenID Connect

OAuth 2.0

SAML

Spring

Jakarta EE

GraphQL

NestJS

Terraform

Docker

Kubernetes

.NET

Node.js

Go

PHP

Java

Python
The Benefits of Partnering with Erbis
By choosing Erbis as your cybersecurity partner, you'll enjoy:
- Top Security Measures: Triple legal protection for your intellectual property and additional guarantees of regulatory compliance.
- ISO 27001 Certified: Clear proof of our commitment to protecting your data
- Extensive Practical Experience: Cybersecurity is a part of our daily routines as a custom software development company, so all our recommendations are backed by practical experience, not only theoretical best practices.
- Cost-Efficiency: We deliver high-quality solutions within your budget and timeline.
- Strategic Guidance: We help define your cybersecurity strategy, anticipate challenges, and guide you toward success.
Industries and Domain Expertise
We specialize in two key industries where our expertise is unmatched:
- Supply Chain
- LegalTech
In addition, we support startups across various industries, leveraging our cybersecurity expertise to build products and resilient security infrastructures.
Our core domain expertise:
- GRC Solutions
- AI, Big Data & Machine Learning
- Cloud and DevOps
- Legacy System Support & Modernization
- Digital Transformation & Automation
What Our Clients Say
Early testing shows that the platform is behaving as expected. The team delivered on time and to specifications, often suggesting add-ons to improve functionality. The project management tools they employed were sufficient for the project’s needs. The relationship was a reciprocal one.
What Our Clients SayThe speed at which Erbis Cloud Services ramped up to understand the technical requirements and the business was impressive to the client. The communication and trustworthiness of Erbis has been a unique asset to the client.
See Review on ClutchAwards and Recognition
Our Commitment to Excellence Recognized