Anti-phishing software for a US security software provider
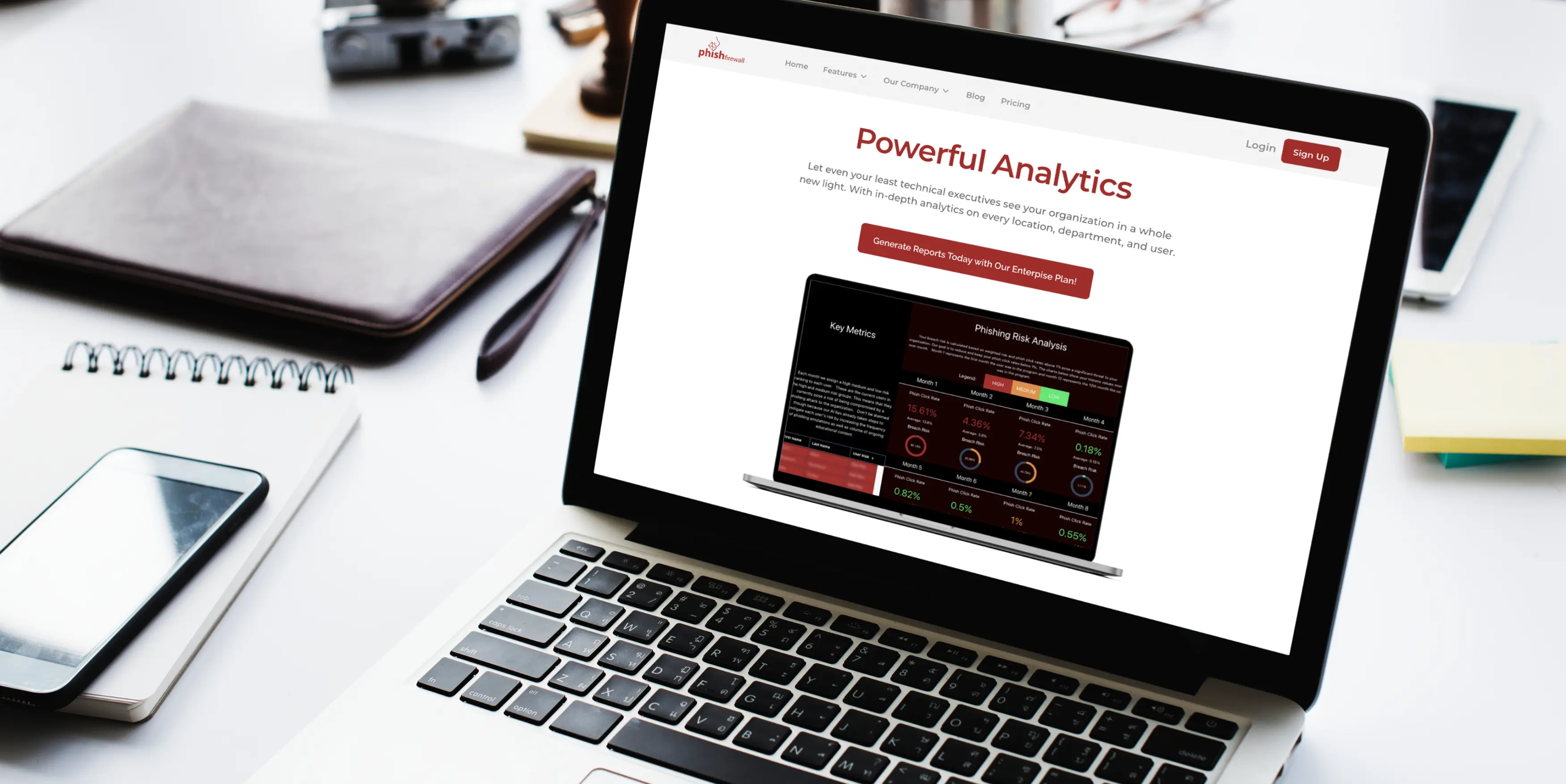
Erbis has created a full-featured product that prevents phishing attacks. What follows are the project details and a discussion of the challenges, technologies, and business outcomes involved in developing the product.
Challenge
Phishfirewall, an established security awareness software provider, chose Erbis to enhance a product that would prevent phishing attacks through the education of employees. The client already had a solution on a no-code platform, which, however, had many significant operational limitations. We proposed the building of a classic SaaS using a high-code approach. The client supported our idea, and we started work.
One of the challenges we faced was transferring data from an existing platform to a new high-code framework. We also needed to create a system that quickly adapts to new types of phishing.
It is apparent that modern hackers evolve as quickly as new technologies, so a system that provides anti-phishing training and security awareness must supply users with the latest data and updates.
Pre-development stage
We began by studying the existing platform and technical documentation of the project. Our business analyst (BA) also conducted a series of interviews with the client to assess the project goals, understand the target audience, and draw up a project roadmap. A thorough analysis helped us identify key pain points in the existing solution and prioritize features critical to educating users on phishing threats.
It was agreed to assign three full-stack developers to work on the project. They were working under the supervision of our CTO, who managed the technology strategy and was always in touch with the client. Transparent communication kept us on the same page with the client throughout the project implementation with zero misunderstandings and conflicts.
Development flow
We chose a combination of low-code and high-code tools to implement the product quickly and efficiently. Our team developed the Mailer, back office, and a proprietary API.
The Mailer is a functionality that sends emails to users (the company's employees) through Pardot (Salesforce) Mailer.
- It synchronizes data such as segments, users, and email templates from Pardot to the app database
- selects today's potential recipients of phishing emails
Tech stack:
- Frontend: Retool (low-code)
- Backend: Node.js and Express.js, PostgreSQL
- Database: PostgreSQL
- Cloud: Google Cloud via Docker
The back office serves as the administrative hub of the product, enabling users to manage various aspects of the application.
Tech stack:
- Frontend: React.js, Chart.js, MUI
- Backend: Node.js with many additional libraries such as Express, Axios, Passport, Sequelize, and Stripe
- Integrated into Taiga API to create Phish Reports
The proprietary API allows users to interact with their company data, mailing history, user actions, phishing reports, etc
Since we had a relatively small project with a predictable set of features, we chose the waterfall SDLC. Our development flow was divided into phases, in which we gathered requirements and developed, tested, and deployed certain functionality. After that, we moved on to the next phase and developed new functionality.
Tech stack
- Node.js
- Express.js
- React
- PostgreSQL
- Retool
- Docker
- Google Cloud
End product
Our solution for Phishfirewall is an educational app that enhances users' awareness about different types of phishing attacks and thereby reduces the number of data leaks and financial losses for the organization.
The app logic is as follows:
Every 3 minutes, the app selects potential email recipients and sends emails to them. There are six email flows:
- Introduction- an email with introductory information and a choice of key phrase for the user
- Phishing - simulation of phishing emails
- Training - training emails
- Mixed - a combination of training and phishing
- Administrative - announcement emails for BackOffice administrators
Every 10 minutes, user actions are extracted from the Pardot API: opens and clicks.
If a user clicks on a link in a phishing email, it is displayed as a "click." Next, a warning email is sent to the user, alerting them about the danger.
If the user doesn't click on the link within a specified period of time, they receive a congratulatory email.
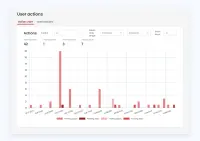
All user actions (opens and clicks) are stored in the database. Every first day of the month, statistics about each user are updated and sent to Pardot.
The Results
By offering an anti-phishing application to its customers, our client guarantees that the phish click rate after six months will be less than 1%. For comparison, the phish click rate of competitors is still more than 5% after six months.
In addition, the use of anti-phishing software brings many other benefits, such as
- Increased employee engagement
- Reduced phishing vulnerabilities
- Improved cybersecurity culture

Looking to develop an anti-phishing app?
Anti-phishing software is a robust defense against the growing menace of phishing attacks. It detects and blocks fraudulent attempts to deceive individuals into divulging confidential information, such as login credentials or financial details.
Organizations are increasingly looking to adopt anti-phishing software because they want to protect valuable data. And since human unawareness is a decisive factor for a successful phishing attack, employee education is crucial in building a company's security strategy.
At Erbis, we have extensive experience developing security solutions. We work with companies that create data protection software for their own needs and software providers that offer their products to customers. If you are looking for a trusted partner in cybersecurity, contact us now, and let's start a successful project together.












